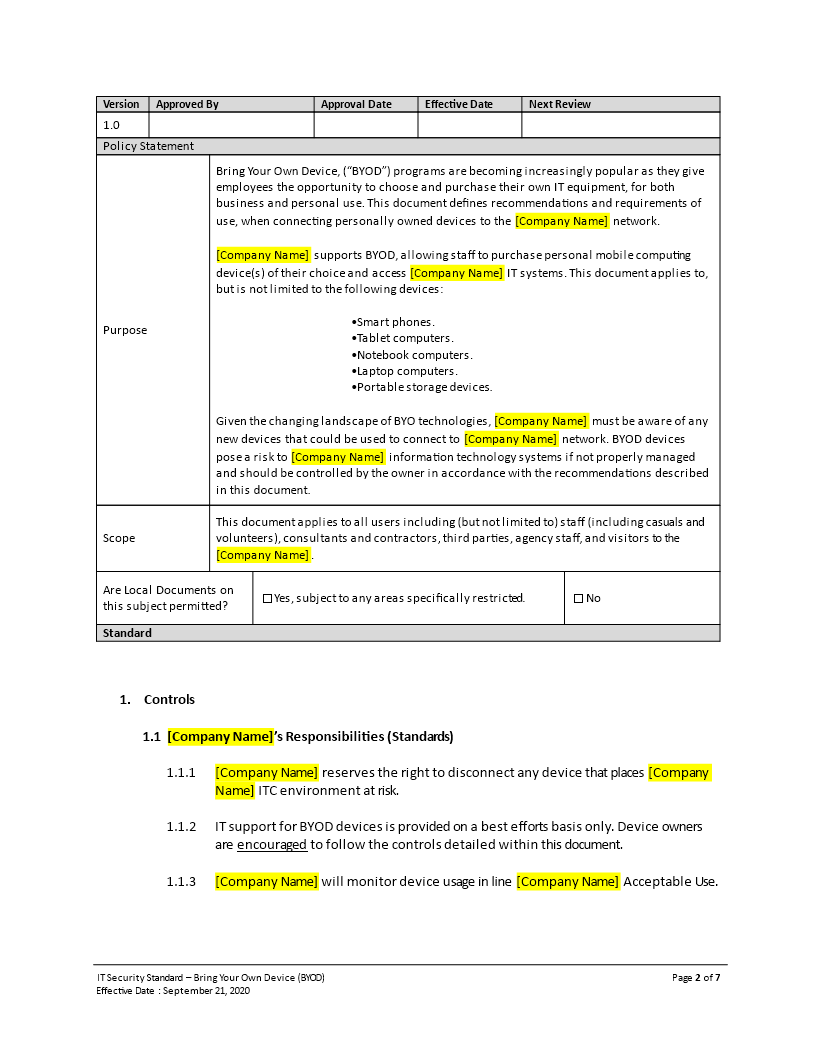
GDPR Bring Your Own Device BYOD Policy
Review Rating Score
What does BYOD stand for?
Bring Your Own Device (BYOD) — also is called Bring Your Own Technology (BYOT), Bring Your Own Phone (BYOP), or Bring Your Own Personal Computer (BYOPC)—refers to being allowed to use one's personally owned device, rather than being required to use an officially provided device. This can be a laptop, mobile device, smart device, or any other ICT related device that you also use personal but now also will use at work. So it is best described as a situation where employees are using their own devices for work.
Why do you need a BYOD policy?
Although BYOD as many advantages like increased productivity, reduced company device costs, increase employee loyalty, and more easy employee incoming and outcoming transition, it also brings several new challenges that need to be taken care of. For example:
- Maintain employee privacy
- Business network security
- Device security
- Data security
- Mis usage
- Reimbursement
So there must be a structure for security and data usage for BYOD to work. This is where implementing a BYOD Policy comes into play. Employee must mandate device controls such as passwords, pins, or biometric settings in order to enable access to the device. Only authorized people should be permitted to use these devices. Data encryption should be used to protect sensitive information. In some cases it is even necessary to mandate that only essential apps should be installed on employee-owned devices to reduce the risk of exposure to malware or data breaches. Also, there must be a set of rules in place for when employees depart the company to ensure all company access and material is securely removed from their devices. A thorough BYOD policy will include the most important rules and regulations regarding employ usage of their own devices.
Is a BYOD policy required?
Having a well-implemented BYOD policy in place is compulsory according to the EU General Data Protection Regulation (GDPR) directive. GDPR is a directive that provides guidelines on (personal) data protection rights to all data processors of (personal) data of EU citizens. Regardless of where their data is processed. It aims to make Europe fit for the digital age and it affects all companies that save personal data from European citizens.
Are you looking for this Bring Your Own Device Policy (BYOD) Policy? Is your organization already GDPR proof? Please note the original enforcement date was 25 May 2018, at which time those organizations in non-compliance may face heavy fines. If you did not yet implement a BYOD policy than this is a good time to start. The easy way is by downloading this BYOD-Policy now.
Is the template content above helpful?
Thanks for letting us know!
Reviews
Kym Blankenship(9/27/2020) - USA
Exactly what I wanted, good content for my problen
Diego Hoffman(9/27/2020) - USA
I just browsed on the website, find some great documents
Joette Mcclure(9/27/2020) - USA
I like the website and the file
Last modified
Delivery Instant Download
Your file will be available for download once payment is confirmed. Here's how.
Our Latest Blog
- The Importance of Vehicle Inspections in Rent-to-Own Car Agreements
- Setting Up Your E-mail Marketing for Your Business: The Blueprint to Skyrocketing Engagement and Sales
- The Power of Document Templates: Enhancing Efficiency and Streamlining Workflows
- Writing a Great Resume: Tips from a Professional Resume Writer
Template Tags
Need help?
We are standing by to assist you. Please keep in mind we are not licensed attorneys and cannot address any legal related questions.
-
Chat
Online - Email
Send a message
You May Also Like

Event Risk Management Plan

Business Policy Template - Create Your Custom Policy

FDA Strategic Action Plan for Safety of Products

Inclement Weather Policy for Sb Policy: School Guidelines for Students and Weather

Motorcycle Policy, Safety, Service & Training - CNGO

HR Corporate Strategic Plan: Action and Engagement
Pregnancy Diet: PDF, Medications, and Avoidance Guidelines

Effective Staff Training Agenda for Emergency Preparedness and Disaster Management

Financial Statement Controls - Streamlining Finance Workflow
University Smoking Policy: Promoting Health and Enforcing Smoke-Free Campus

Employee Disciplinary Policy - April | Fair Hearing Process

Policy for Letter of Intent - Guidelines for Letter, Promotion, and Title for Faculty Chair
Assess Your Company's Employees and Gather Valuable Comments for Improvement

Marion Environmental Management: Your Comprehensive Environmental Policy Solution

Drug Testing Consent Agreement Form - Policy for Controlled Substance Testing at Citadel

Information Security Procedures: Ensuring Agency Safety and Compliance