/5da95268-004f-4816-a1b3-067335bf9ee6.png)
Network Protection: Comprehensive Info Security Policy for Systems & Computers
Review Rating Score
Welcome to BizzLibrary.com, your go-to source for comprehensive information on network protection and information security policies. In today's digital landscape, it is crucial for businesses to prioritize the security of their information systems and ensure the protection of sensitive data. Our Network Protection And Info Security Policy template serves as a valuable resource to help you establish a robust security framework.
The Importance of Network Protection and Information Security
In this interconnected world, organizations rely heavily on computer systems and networks to store, process, and transmit data. This data can include sensitive information such as customer details, financial records, and proprietary business data. It is imperative that businesses implement robust security measures to safeguard this information from unauthorized access, disclosure, alteration, or destruction.
Key Components of a Network Protection And Info Security Policy
A comprehensive Network Protection And Info Security Policy covers various aspects of information security within an organization. Here are some key components:
- Access Control: This section outlines the procedures and requirements for granting access to the organization's information systems and data. It covers user authentication, password policies, and access levels based on job roles.
- Security Awareness and Training: Employees play a vital role in maintaining information security. This component focuses on creating awareness about the importance of security measures and provides guidelines for training employees on information security best practices.
- System Monitoring and Incident Response: It is crucial to have mechanisms in place to detect and respond to potential security incidents. This section defines the monitoring processes, incident handling procedures, and reporting mechanisms to mitigate potential threats.
- Data Backup and Disaster Recovery: This component addresses the importance of regular data backups, as well as procedures for disaster recovery in the event of system failures, natural disasters, or other disruptive incidents.
- Physical Security: Information security is not limited to digital assets. This section covers physical security considerations, such as restricting access to server rooms, protecting physical storage media, and preventing unauthorized removal of equipment.
Download Your Network Protection And Info Security Policy Template
To ensure the secure operation of your information systems and protect the confidentiality, integrity, and availability of your data, it is essential to have a well-documented Network Protection And Info Security Policy in place. Visit BizzLibrary.com now and download our customizable PDF template.
Empower your organization with the necessary tools to mitigate security risks and establish a solid foundation for information security. Take the first step towards a secure digital future!
Is the template content above helpful?
Thanks for letting us know!
Reviews
Coleen Williams(11/7/2023) - DEU
Perfect! Can I buy you a drink
Last modified
Our Latest Blog
- The Importance of Vehicle Inspections in Rent-to-Own Car Agreements
- Setting Up Your E-mail Marketing for Your Business: The Blueprint to Skyrocketing Engagement and Sales
- The Power of Document Templates: Enhancing Efficiency and Streamlining Workflows
- Writing a Great Resume: Tips from a Professional Resume Writer
Template Tags
Need help?
We are standing by to assist you. Please keep in mind we are not licensed attorneys and cannot address any legal related questions.
-
Chat
Online - Email
Send a message
You May Also Like

Event Risk Management Plan

Business Policy Template - Create Your Custom Policy

FDA Strategic Action Plan for Safety of Products

Inclement Weather Policy for Sb Policy: School Guidelines for Students and Weather

Motorcycle Policy, Safety, Service & Training - CNGO

HR Corporate Strategic Plan: Action and Engagement
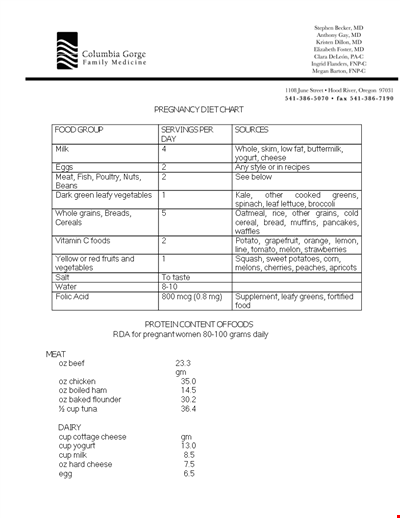
Pregnancy Diet: PDF, Medications, and Avoidance Guidelines

Effective Staff Training Agenda for Emergency Preparedness and Disaster Management

Financial Statement Controls - Streamlining Finance Workflow
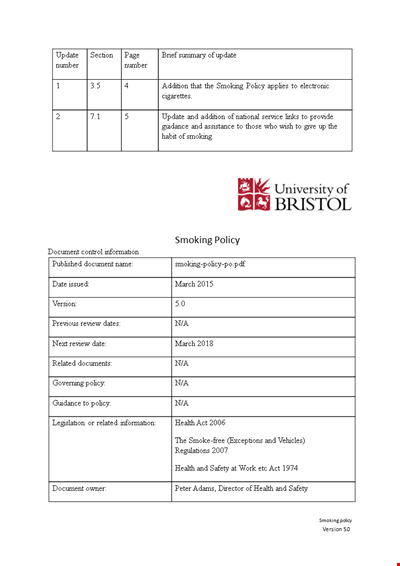
University Smoking Policy: Promoting Health and Enforcing Smoke-Free Campus

Employee Disciplinary Policy - April | Fair Hearing Process

Policy for Letter of Intent - Guidelines for Letter, Promotion, and Title for Faculty Chair
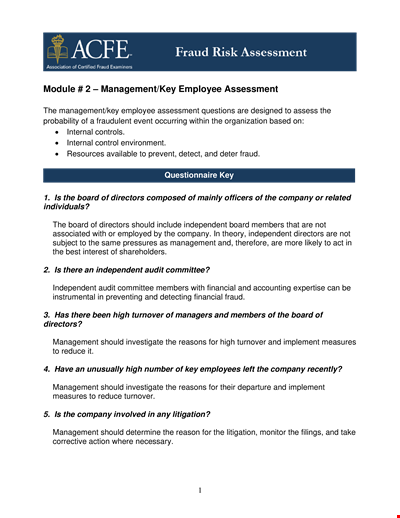
Assess Your Company's Employees and Gather Valuable Comments for Improvement

Marion Environmental Management: Your Comprehensive Environmental Policy Solution

Drug Testing Consent Agreement Form - Policy for Controlled Substance Testing at Citadel

Information Security Procedures: Ensuring Agency Safety and Compliance