/62dbfe76-9acd-43ad-93c6-6f80956a9fa6.png)
Comprehensive Company Security Policy for Access Control - Maximum Security
Review Rating Score
As a company, it is your responsibility to ensure the security of your data and access to it. With the increasing risk of cyber-attacks and data breaches, having a comprehensive security policy in place is not an option but a necessity.
What is a Security Policy?
A security policy is a document that outlines a company's rules, guidelines, and procedures for protecting its information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction. It is a set of guidelines that helps ensure the confidentiality, integrity, and availability of sensitive data.
Why Must You Have a Security Policy?
Hackers and cyber attackers are always looking for loopholes in the security systems of companies, which can compromise sensitive data and put businesses at risk. In addition, companies need to fulfill legal requirements related to data protection, personal data, and privacy regulations. Here are some reasons why having a security policy is crucial:
- Protects Sensitive Data: A security policy establishes procedures for accessing, storing, and sharing sensitive information, making sure that it is protected from unauthorized access and use. It also defines acceptable-use policies, which specify how employees must behave while using IT systems, thus reducing the human errors that can lead to a security breach.
- Ensures Compliance: A security policy ensures that a company adheres to relevant legal requirements and compliance obligations, including industry-specific regulations, data protection, and privacy laws.
- Increases Trust and Credibility: Having a robust security policy in place can help build the trust of customers, business partners, and stakeholders, who want to ensure that their data is protected. A security policy can improve a company's reputation, potentially leading to new business opportunities.
- Reduces Security Risks: A security policy identifies potential threats and risks to your company's data, guiding the implementation of protective measures, such as firewalls or data encryption, to prevent security breaches and cyber-attacks.
Download Your Security Policy Template
Don't leave your company's data vulnerable to cyber-attacks and security breaches. Our professionally drafted security policy template in DOCX format is designed to help you create a robust security policy that meets your business needs. It includes clear guidelines for protecting your company's information and information systems, with sample policies and procedures to get you started.
Visit BizzLibrary.com now to download your security policy template and access our wide range of business document templates, including security agreements, data privacy policies, and more. Secure your company's future with effective security policies and procedures.
Is the template content above helpful?
Thanks for letting us know!
Reviews
Katelyn Golden(7/8/2023) - DEU
Thank you for the letter!!
Author. Content was provided by:
Elizabeth Davis
Elizabeth is from the sunny desert city of Phoenix, Arizona. She is thrilled to connect with professionals and like-minded individuals who share a passion for social technologies, content creation, and the exciting possibilities that AI brings to the world of social media. Her hobbies are hiking, climbing, and horse riding. Elizabeth has a master's degree in Social Technologies that she received at the ASU (Arizona State University). As a freelancer, she mostly contributes content related to IT. This includes articles on templates and forms provided by our community.
Follow Elizabeth
Last modified
Our Latest Blog
- The Importance of Vehicle Inspections in Rent-to-Own Car Agreements
- Setting Up Your E-mail Marketing for Your Business: The Blueprint to Skyrocketing Engagement and Sales
- The Power of Document Templates: Enhancing Efficiency and Streamlining Workflows
- Writing a Great Resume: Tips from a Professional Resume Writer
Template Tags
Need help?
We are standing by to assist you. Please keep in mind we are not licensed attorneys and cannot address any legal related questions.
-
Chat
Online - Email
Send a message
You May Also Like

Event Risk Management Plan

Business Policy Template - Create Your Custom Policy

FDA Strategic Action Plan for Safety of Products

Inclement Weather Policy for Sb Policy: School Guidelines for Students and Weather

Motorcycle Policy, Safety, Service & Training - CNGO

HR Corporate Strategic Plan: Action and Engagement
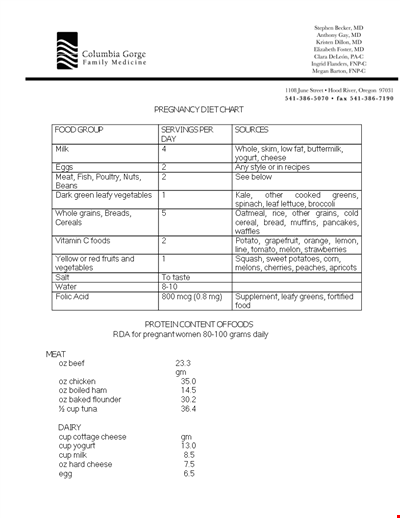
Pregnancy Diet: PDF, Medications, and Avoidance Guidelines

Effective Staff Training Agenda for Emergency Preparedness and Disaster Management

Financial Statement Controls - Streamlining Finance Workflow
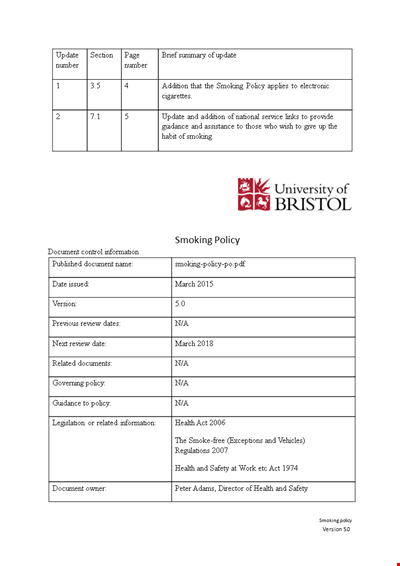
University Smoking Policy: Promoting Health and Enforcing Smoke-Free Campus

Employee Disciplinary Policy - April | Fair Hearing Process

Policy for Letter of Intent - Guidelines for Letter, Promotion, and Title for Faculty Chair
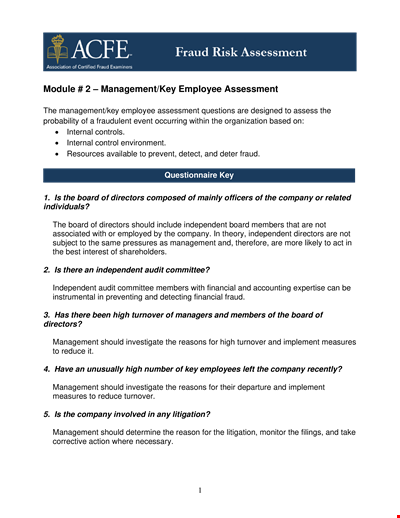
Assess Your Company's Employees and Gather Valuable Comments for Improvement

Marion Environmental Management: Your Comprehensive Environmental Policy Solution

Drug Testing Consent Agreement Form - Policy for Controlled Substance Testing at Citadel

Information Security Procedures: Ensuring Agency Safety and Compliance