/69601514-9eed-46b3-b306-d43e8b3c9844.png)
Patient Security Policy: Incident, HIPAA, and Breach Prevention
Review Rating Score
Protecting sensitive patient information is of utmost importance in the healthcare industry. A comprehensive security policy is critical in ensuring that protected health information (PHI) is managed securely and that measures are taken to prevent data breaches and incidents.
What is a Security Policy for PHI?
A security policy is a formal document which establishes guidelines and procedures concerning the processing, handling, accessing, and sharing of PHI. The policy ensures that all necessary security measures have been implemented to protect the confidentiality, integrity, and availability of PHI.
Why is a Security Policy for PHI Necessary?
A security policy for PHI is necessary to:
- Comply with HIPAA Regulations: The Health Insurance Portability and Accountability Act (HIPAA) outlines strict requirements for protecting PHI. A security policy ensures that healthcare organizations or individuals handling PHI are in compliance with HIPAA regulations and are taking adequate measures to safeguard patient information.
- Maintain Patient Trust: Patients entrust healthcare organizations with their private and sensitive information. A security policy ensures that the confidentiality and privacy of their information is protected, leading to increased trust and confidence in the healthcare system.
- Prevent Data Breaches and Incidents: A security policy establishes the procedures and safeguards necessary to prevent data breaches and incidents. Policies and procedures are in place to identify and investigate security incidents, including procedures for reporting and mitigating security breaches.
What Should a Security Policy for PHI Include?
A comprehensive security policy for PHI should include:
- Roles and Responsibilities: The policy should define the roles and responsibilities of individuals involved in the handling, processing, accessing, and sharing of PHI.
- Security Measures: The policy should outline the physical, technical, and administrative safeguards in place to protect PHI, such as access controls, encryption, and monitoring systems.
- Breach Notification Procedures: In the event of a breach, the policy should include detailed procedures for investigating, reporting, and mitigating the breach.
- Training and Awareness: The policy should outline the training and awareness programs in place to educate staff on proper handling and protection of PHI.
- Risk Assessment and Management: The policy should establish procedures for assessing and managing risks associated with the handling of PHI.
Download Your Security Policy for PHI
At BizzLibrary.com, we offer a comprehensive, customizable security policy template for download in DOCX format. Our policy template is designed to meet HIPAA requirements and ensure the security of PHI. Download our template today and start protecting sensitive patient information!
Visit BizzLibrary.com now to access a wide range of business and healthcare document templates, including security policies, incident response plans, and more.
Is the content above helpfull?
Thanks for letting us know!
Reviews
Sheri Freeman(7/4/2023) - DEU
Perfect document templat
Last modified
Our Latest Blog
- The Importance of Vehicle Inspections in Rent-to-Own Car Agreements
- Setting Up Your E-mail Marketing for Your Business: The Blueprint to Skyrocketing Engagement and Sales
- The Power of Document Templates: Enhancing Efficiency and Streamlining Workflows
- Writing a Great Resume: Tips from a Professional Resume Writer
Template Tags
Need help?
We are standing by to assist you. Please keep in mind we are not licensed attorneys and cannot address any legal related questions.
-
Chat
Online - Email
Send a message
You May Also Like

FDA Strategic Action Plan for Safety of Products

Inclement Weather Policy for Sb Policy: School Guidelines for Students and Weather

Motorcycle Policy, Safety, Service & Training - CNGO

HR Corporate Strategic Plan: Action and Engagement
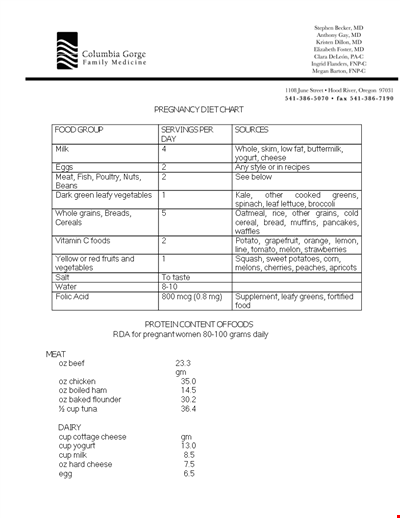
Pregnancy Diet: PDF, Medications, and Avoidance Guidelines

Effective Staff Training Agenda for Emergency Preparedness and Disaster Management

Financial Statement Controls - Streamlining Finance Workflow
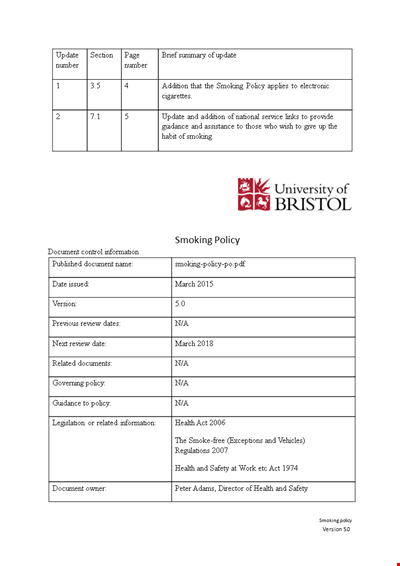
University Smoking Policy: Promoting Health and Enforcing Smoke-Free Campus

Employee Disciplinary Policy - April | Fair Hearing Process

Policy for Letter of Intent - Guidelines for Letter, Promotion, and Title for Faculty Chair
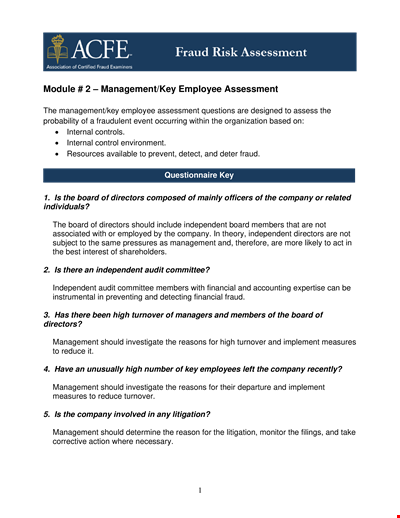
Assess Your Company's Employees and Gather Valuable Comments for Improvement

Marion Environmental Management: Your Comprehensive Environmental Policy Solution

Drug Testing Consent Agreement Form - Policy for Controlled Substance Testing at Citadel

Information Security Procedures: Ensuring Agency Safety and Compliance

Interim NOAA Training Policy: Employee Training & Development for Employees

New Employee Relocation Policy: Expenses, University Support | Company Name