CyberSecurity Job Description
Review Rating Score
An effective Security Specialist job description is vital when attracting the right talents. Use this Security Specialist Job Description template for your inspiration when you need to create a job posting that is clear and concise.
What is Cyber Security job description?
A CyberSecurity professional is an expert in technology that prevents data leaks to external sources, and manages the information flows internally as well. He/she uses their technology expertise and training to ensure that an organization’s sensitive data remains secure from both internal and external threats and risks. This requires a keen awareness of specific IT risks, including hacks, and other cyber crimes or unauthorized usage of the organizations' systems. A CyberSecurity Specialist is therefore responsible for the upkeep of an organization's automated security systems and employee identity card systems. They keep rigorous vigil over company data from entry to storage to exit, and create strategies to both proactive prevent and systematically react to breaches. The specialist serves as the primary contact point for security system concerns. As a Security Specialist, you will teach workers on how to utilize and understand security technologies. A bachelor's degree may be required. Furthermore, Security Specialists usually report to a supervisor or manager. Typically, multiple years of similar experience is required to become a Security Specialist. A subject matter expert in difficult technological and business issues. Work is quite self-sufficient. May take up the position of team leader for the work group.
This sample CyberSecurity Job description explainer offers guidance on key sections that are important to include for clarity, as well as suggestions for promoting the position. It provides a list of duties, responsibilities, tasks, requirements, demands for setting job expectations and the employee's ability to perform the work as described. However, it’s often not construed as an exhaustive list of all functions, responsibilities, skills and abilities.
What does a CyberSecurity Professional do?
Responsibilities:
- Implementing and forming safety rules and procedures;
- Monitoring network activity in order to find weak areas;
- Responding to data breaches and security threats in mean of IT;
- Guard all company data, particularly sensitive data, from both internal and external threats by designing broad defenses against would-be intruders;
- Take the lead on day-to-day monitoring for unusual activities, implement defensive protocols, and report incidents;
- Collaborate with other members of the cybersecurity team to develop new protocols, layers of protection, and other both proactive and defensive systems that stay one step ahead of cyber criminals;
- Maintain security guidelines, procedures, standards, and controls documentation;
- Maintain a working knowledge of current cybercrime tactics;
- Collect data on current security measures for risk analysis and write regular systems-status reports;
- Constantly monitor for attack and run appropriate defensive protocols if breaches occur;
- etc (see samples in download file).
Qualifications and skills:
- Degree in computer science, cyber security, or a related subject or degree in information systems, information technology or related field;
- 5 years experience in cybersecurity at a mid- to large-size business;
- Strong knowledge of IT, including hardware software and networks;
- A meticulous eye for detail and ability to multitask in a fast-paced environment;
- Excellent verbal and written communication skills;
- Strong critical thinking, problem-solving, logic, and forensics skills;
- Ability to work successfully in both individual and team settings;
- Ability to think like a hacker in order to stay one step ahead;
- Knowledge of security frameworks (for example, the NIST Cybersecurity Framework) and risk management techniques;
- Understanding of patch management, firewalls, and intrusion detection and prevention systems;
- Knowledge of public key (PKI) and cryptography methods are required;
- An analytic intellect with strong problem-solving skills;
- Etc (see example job descriptions).
Is the template content above helpful?
Thanks for letting us know!
Reviews
Ferdy f(12/24/2021)
This is such a nice file with IT security job descriptions, thasnk
Ashely Chang(12/24/2021) - DEU
I wan tto express my gratitude
Lucy Gilbert(12/24/2021) - AUS
You deserve more stars, but there are none
Shanika Spears(12/24/2021) - DEU
Thank you for the Doc!!
Author. Content was provided by:
Elizabeth Davis
Elizabeth is from the sunny desert city of Phoenix, Arizona. She is thrilled to connect with professionals and like-minded individuals who share a passion for social technologies, content creation, and the exciting possibilities that AI brings to the world of social media. Her hobbies are hiking, climbing, and horse riding. Elizabeth has a master's degree in Social Technologies that she received at the ASU (Arizona State University). As a freelancer, she mostly contributes content related to IT. This includes articles on templates and forms provided by our community.
Follow Elizabeth
Last modified
Our Latest Blog
- The Importance of Vehicle Inspections in Rent-to-Own Car Agreements
- Setting Up Your E-mail Marketing for Your Business: The Blueprint to Skyrocketing Engagement and Sales
- The Power of Document Templates: Enhancing Efficiency and Streamlining Workflows
- Writing a Great Resume: Tips from a Professional Resume Writer
Template Tags
- cyber security job description
- information security analyst job description cyber security analyst job description
- cyber security engineer job description
- soc analyst job description
Need help?
We are standing by to assist you. Please keep in mind we are not licensed attorneys and cannot address any legal related questions.
-
Chat
Online - Email
Send a message
You May Also Like

Treasurer Job Description for Foundation

Product Manager Real Estate Job Description

Restaurant Waiter Job Description | Manager | Customer Service | Serving Customers

Resort Nanny Job Description | Caring for Children, Cleaning, Assisting Parents

School Treasurer Job: Activities & Responsibilities

Pod Nanny Job Description: Experienced Nannies for Your Child's Education and Care

Administrative Job Description Template for Manager | Department | Agency | Administrative

School Secretary Job Description: Office Staff & Personnel for Students

Legal Lawyer Job Description | Find Your Legal Career Here

Free Download: HR First Job Resume Template | University, Experience, Skills, Relevant | Halifax

Dentist Operation Manager Job Description - Dental Program and Appropriate

Download Free General Sales Manager Job Description Template for Retail | Charlie - Charming

Child Caregiver Job Description and Responsibilities for Caring for Children with Knowledge

IT Support Job Description: Software, Hardware, and Production Duties for Computer-related Support
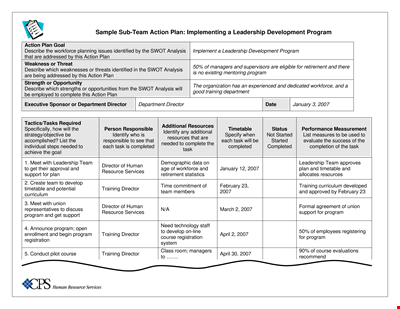
Sub Team Leader Action Plan Template

Dispatcher Purchasing Agent Job Description